The Pitfalls of Using OpenZeppelin's AccessControl for Blacklisting Mechanisms
In the world of smart contract development, security is non-negotiable. Many developers rely on established libraries like OpenZeppelin to build robust and secure applications. A commonly used component is the AccessControl contract, which provides a flexible role-based permission system. However, what many don't realize is that this system is unsuitable for blacklisting mechanisms – and might even pose a significant security risk.
The Seemingly Perfect Tool
At first glance, OpenZeppelin's AccessControl appears to be an ideal solution for blacklisting purposes. The contract offers:
- A sophisticated role system
- Granular permission management
- The ability to define administrators and role holders
- Easy integration into existing smart contracts
Many developers use this mechanism to assign a "BLACKLISTED" role to certain addresses, thereby restricting token transfers. This seems particularly convenient as the contract has already been extensively tested and used in many projects.
The Critical Security Flaw: renounceRole()
What many developers overlook is a critical function called renounceRole() that is included in every AccessControl contract:
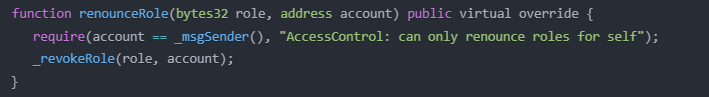
This function allows any address to give up its own role – and therein lies the problem. If an address is placed on the blacklist, the owner of that address can simply call the renounceRole() function and independently remove the "BLACKLISTED" role!
A proper blacklisting mechanism should not offer this possibility. Control over blacklisting should rest exclusively with the protocol administrators.
A Practical Example
Consider the following scenario:
- A token contract uses AccessControl for blacklisting
- A suspicious address is assigned the "BLACKLISTED" role
- Token transfers are restricted for this address
- The owner of the blacklisted address calls renounceRole(BLACKLISTED_ROLE, myAddress)
- The address is no longer blacklisted and can transfer tokens without restrictions again
This simple example shows how the entire blacklisting mechanism can be circumvented with a single function call.
Better Alternatives for Blacklisting Mechanisms
Instead of using AccessControl, developers should implement a mechanism specifically designed for blacklisting. Here are some approaches:
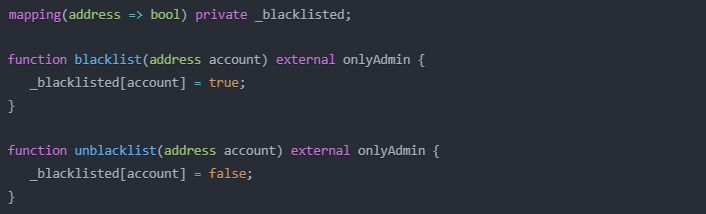
- Dedicated Mapping Structures:
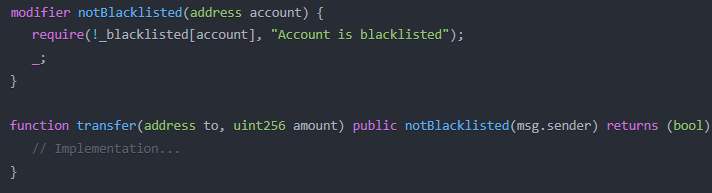
- Modifiers for Transfer Functions:
- Advanced Blacklisting Features:
- Time-based blacklisting
- Restriction of specific actions rather than complete blocking
- Tiered restrictions
Why Professional Smart Contract Audits Are Essential
Such subtle security issues demonstrate the importance of professional smart contract audits. An experienced audit team can:
- Uncover misunderstandings in the use of libraries
- Identify potential vulnerabilities before they are exploited
- Recommend proven implementation patterns
- Improve the overall security architecture
At BailSec, we have analyzed numerous smart contracts and discovered many vulnerabilities in blacklisting mechanisms – including the flawed use of AccessControl.
Conclusion: Security Through Tailored Solutions
OpenZeppelin's libraries are excellent tools, but they must be used for the right purpose. For blacklisting functionality, developers should choose a customized approach that doesn't offer unintended backdoors.
Our proven workflow at BailSec includes not only identifying such issues but also developing robust alternatives that meet the specific requirements of your project.
The blockchain landscape is constantly evolving, and it's crucial to keep pace with the latest security practices. Regularly read our blog for more insights into smart contract security and best development practices.
