Mastering Receive() and Fallback() Functions in Solidity: Security Best Practices
Introduction to Solidity's Special Functions
Smart contracts are the backbone of the Ethereum blockchain, enabling a wide range of applications, from DeFi to NFTs. A critical aspect of smart contract development is the secure management of Ether transfers. In Solidity, Ethereum's primary programming language, two special functions are designed for this purpose: the receive() function and the fallback() function. In this blog post, we'll explore how these functions work, how they handle Ether transfers, and the risks, such as Denial-of-Service (DoS) attacks, that can arise if they're not implemented correctly.
What Is the receive() Function in Solidity?
The receive() function is a special function in Solidity that is triggered when a smart contract receives Ether without any accompanying data. It is marked with the external payable keywords, indicating that it can accept Ether. Here's a simple example:
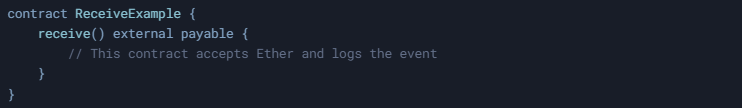
In this example, the contract accepts Ether and can implement additional logic, such as logging the event or emitting an event. If a receive() function is not defined but a fallback() function exists, the fallback() function will handle the Ether transfer. The receive() function is essential for ensuring that your smart contract processes Ether transfers correctly. To learn more about smart contract security, check out our audit services at https://bailsec.io/#audits.
What Is the fallback() Function in Solidity?
The fallback() function is another special function in Solidity that is called when a smart contract is invoked with data that doesn't match any existing function signature, or when Ether is sent without a matching function and no receive() function exists. It can also be defined with external payable to accept Ether, or it can be designed to reject Ether transfers. Here's an example:
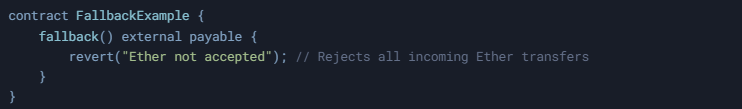
In this case, the contract rejects all incoming Ether transfers by using the revert() statement. The fallback() function is particularly useful for handling unknown calls, but it can also introduce security risks if not implemented carefully. Our smart contract reviews can help you mitigate such risks: https://bailsec.io/#reviews.
Rejecting Ether Transfers: Enhancing Security Measures
There are scenarios where a smart contract should reject Ether transfers, such as when a certain balance is reached or if the transfer is unauthorized. This can be achieved by using the revert() statement in the receive() or fallback() function. Rejecting Ether can be a crucial security mechanism to prevent unwanted interactions. If you need assistance with securely implementing such mechanisms, take a look at our services at https://bailsec.io/#services.
Understanding DoS Attacks via Failed Refunds
A significant security risk when using receive() and fallback() functions is the potential for Denial-of-Service (DoS) attacks. Imagine a smart contract that performs an action and then needs to refund Ether to users. If the receiving contract's fallback() function is manipulated to reject the refund, the refund fails. This can cause the original contract to become stuck, unable to process further transactions. Such attacks can have devastating effects, especially in DeFi protocols that rely on seamless transactions.
To avoid such risks, it's critical to carefully review interactions with external contracts and implement robust refund mechanisms. Our workflows provide a structured approach to identifying and addressing such security issues: https://bailsec.io/#workflow.
Best Practices for Using receive() and fallback()
To ensure the security of your smart contract, consider the following best practices:
Minimize Logic in Special Functions
Keep these functions as simple as possible to reduce the risk of errors or attacks.
Use revert() When Necessary
If your contract should not accept Ether under certain conditions, implement clear rejection logic.
Test Interactions with External Contracts
Ensure your contract can handle various scenarios, including failed refunds.
Conduct Regular Security Audits
Regular audits can uncover potential vulnerabilities before they are exploited.
For more insights on smart contract security, visit our blog for additional articles and resources: https://bailsec.io/#blog.
Conclusion
The receive() and fallback() functions are essential components of Solidity smart contracts, enabling secure Ether transfer management. However, improper implementation can lead to severe security risks, such as DoS attacks. By following best practices and conducting thorough audits, developers can mitigate these risks and build robust smart contracts. If you need support with developing or auditing your smart contracts, we're here to help at Bailsec: https://bailsec.io/#services.
