An infinite mint attack occurs when an attacker manipulates a smart contract’s code to continuously mint new tokens beyond the authorized supply limit. The attacker exploits a bug or error in a protocol's smart contract to trigger excessive minting beyond the authorized supply limit. Once the desired number of tokens has been minted, the hacker floods the market by swapping these newly minted tokens for other cryptocurrencies or tokens. This type of attack can severely undermine the value of the affected cryptocurrency, leading to market disruption and significant financial loss for investors. Optionally, this often also happens by privileged actors, which is the so called soft-rug.
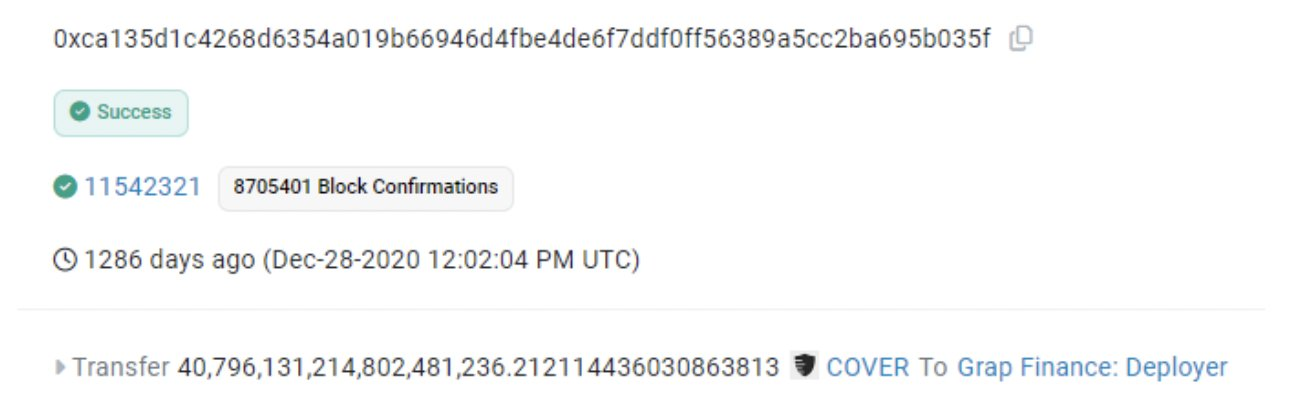
A good example of this type of attack is the Cover protocol, where the hacker created 40 quintillion COVER tokens, consequently dropping the price by 97%. The attacker exploited the Cover protocol's Blacksmith contract by manipulating the deposit and withdrawal functions to exploit an outdated accRewardsPerToken value, allowing the attacker to claim disproportionately large rewards.
Other examples include the BNB bridge infinite mint hack in 2022, Paid Network infinite mint attack, The Qubit Qbridge hack in 2022
How Does It Happen?
Code Vulnerabilities: Poorly written or flawed smart contracts can have vulnerabilities that allow attackers to exploit the minting function. This can happen due to:
> Inadequate access controls
> Logical errors in the minting process
> Lack of proper validation checks
Unchecked Minting Functions: In some cases, the minting function might be left unchecked, allowing anyone to call it and mint new tokens without restrictions.
Manipulated Parameters: Attackers can manipulate parameters passed to the minting function, tricking the contract into minting more tokens than intended.
To prevent infinite mint attacks, projects should conduct frequent smart contract audits by independent security experts to identify and fix vulnerabilities, implement strong access controls with limited minting powers and multi-signature wallets for enhanced security, and use real-time monitoring tools to quickly detect and respond to unusual transaction patterns or sudden increases in token supply.