Detecting honeypot tokens as a non-technical user can be challenging, but with a few steps, you can significantly reduce your risk when considering investing in new tokens on blockchain platforms.
Here’s a practical approach that you can follow:
1. Access the Token's Smart Contract
Visit http://Etherscan.com or any other blockchain explorer that supports the network the token is on.
Search for the token by name or paste its contract address if you have it. This will bring you to the page containing all the details about the token’s smart contract.
Here’s a practical approach that you can follow:
1. Access the Token's Smart Contract
Visit http://Etherscan.com or any other blockchain explorer that supports the network the token is on.
Search for the token by name or paste its contract address if you have it. This will bring you to the page containing all the details about the token’s smart contract.
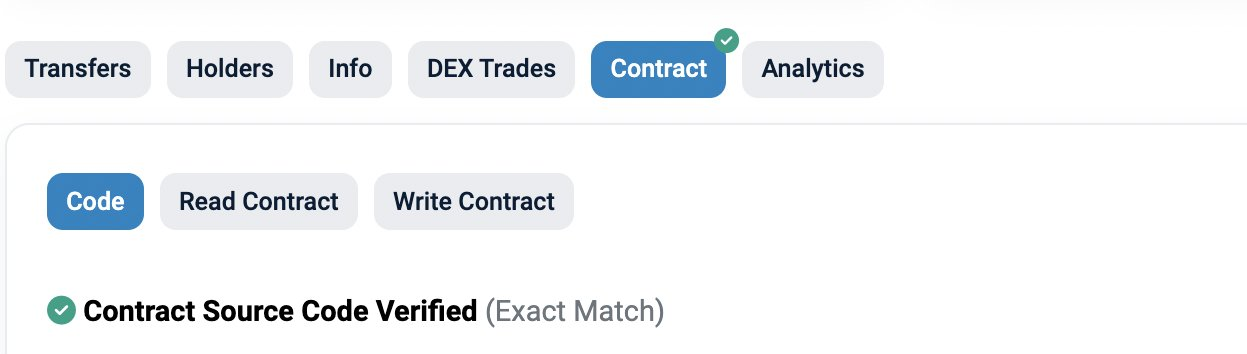
2. Locate the Contract's Source Code
On the token’s page on Etherscan, find the “Contract” section and click on the “Contract” tab to see if the source code is verified. A verified source code will allow you to view the actual written code.
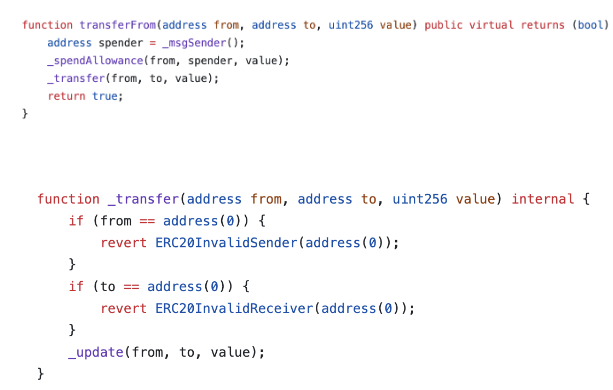
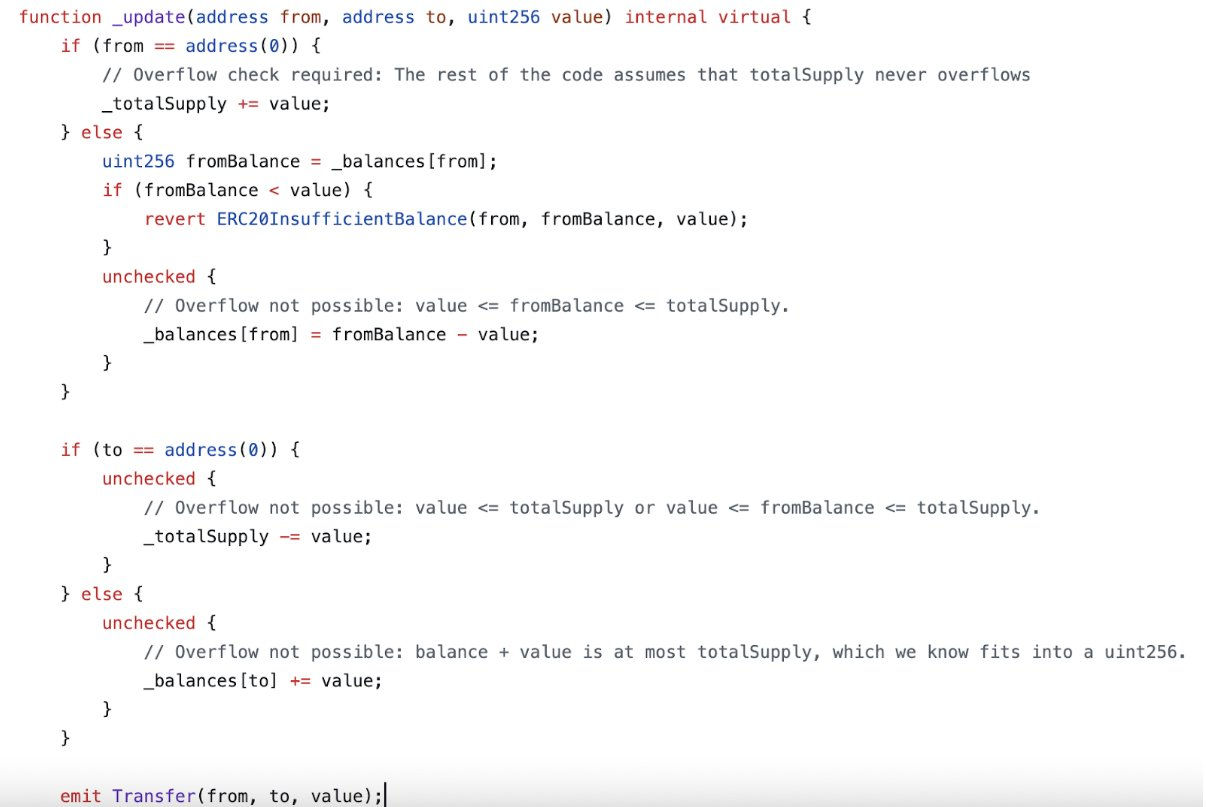
3. Analyze the transferFrom, _transfer and _update Functions
In the contract’s code, look for functions named transferFrom, _transfer and _update. These functions manage how tokens are transferred between addresses.
*Note that this approach only works for ERC20 tokens with the newest @OpenZeppelin version. For older versions, _update may not exist.
4. Use DiffChecker
Open a new tab and go to http://Diffchecker.com
Copy the transferFrom and _transfer code snippets from the token’s contract and paste them on one side of Diffchecker.
Open the standard ERC20 implementation from OpenZeppelin on GitHub.
https://github.com/OpenZeppelin/openzeppelin-contracts/blob/master/contracts/token/ERC20/ERC20.sol
Find the transferFrom and _transfer functions in the standard code and copy the standard implementation and paste it on the other side of Diffchecker.
5. Compare the Code
Hit the "Compare" button in Diffchecker to see any differences between the token’s implementation and the standard. Be cautious if you notice significant deviations, especially those related to restrictions on selling tokens or unusual mechanisms that could prevent selling.
6. Interpreting Results
Significant differences might indicate modifications that could be malicious, such as those allowing only certain addresses (like the developer’s) to execute sales. If you find complex changes and can't determine their purpose, consider them a red flag.
7. Consult Community and Reviews
Research the token on social media, forums, and review sites. See what other investors say about the token and whether anyone has reported issues with buying or selling it.
8. Use Honeypot Checker Tools
Although not foolproof, tools like http://Honeypot.is can provide a quick check. They simulate transactions to see if a token can be sold after being bought.