The question of whether ERC777 tokens are inherently bad or if the issues stem from coding style is often discussed. Let's elaborate what's behind that
ERC777 tokens is the token standard's use of callbacks, specifically through its hooks. These hooks enable a smart contract to react to token transactions, both incoming and outgoing, in real time.
ERC777 tokens is the token standard's use of callbacks, specifically through its hooks. These hooks enable a smart contract to react to token transactions, both incoming and outgoing, in real time.


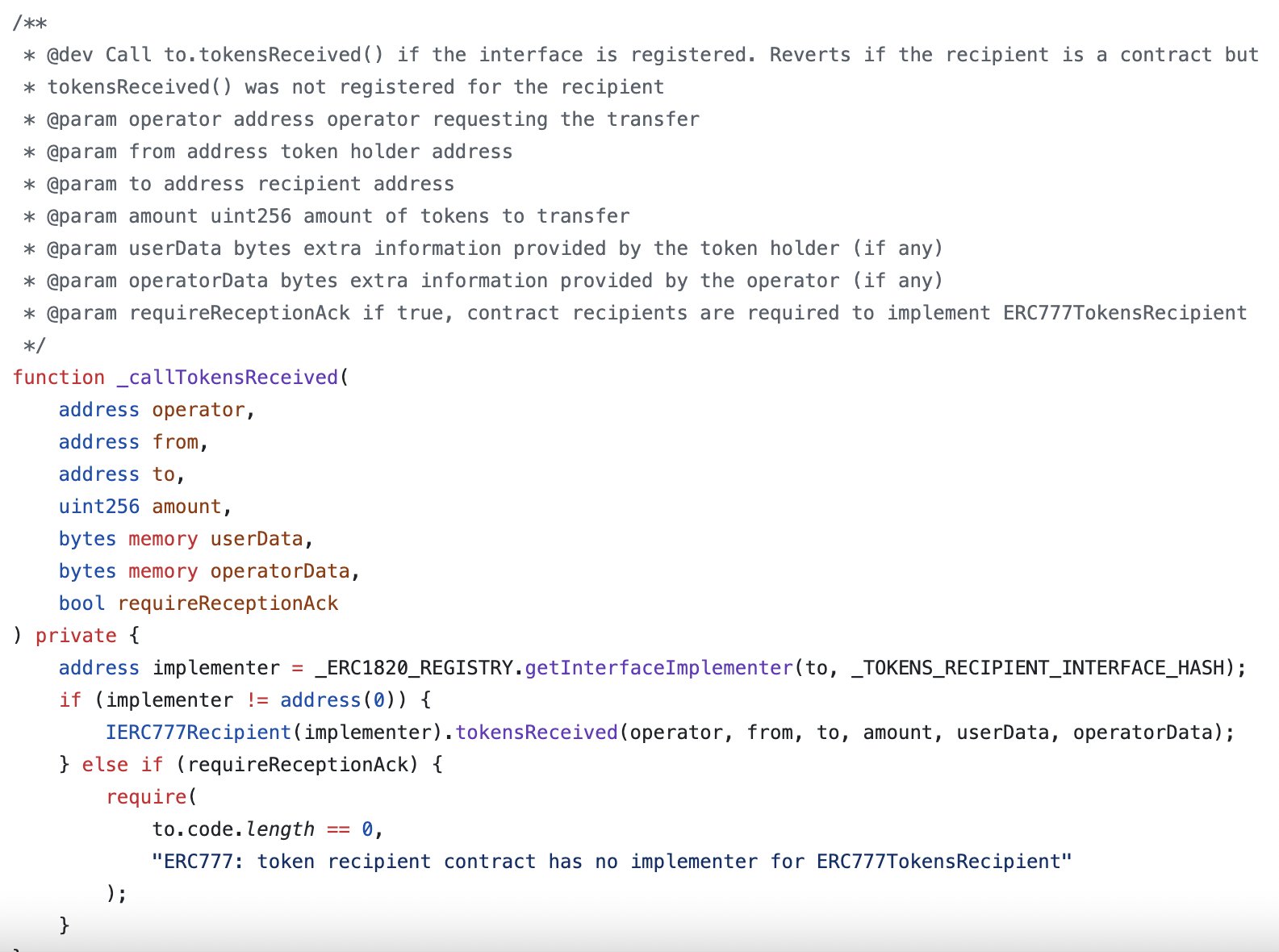
Similar to ERC777, other token standards like gas tokens or ERC721 (notably when using safeTransferFrom) also invoke callbacks to ensure the safe transfer of tokens. The crucial point here is not the token standard itself, but how these callbacks are implemented and interacted with in smart contracts
The potential for abuse or unintended behavior arises when the smart contract's code does not adhere to secure coding principles. Specifically, issues emerge if the contract does not follow the "checks, effects, interactions" pattern or lacks a reentrancy guard.
Checks, Effects, Interactions: This pattern suggests that a function should first perform any necessary checks (e.g., validating input or ensuring prerequisites are met), then make any state changes before finally interacting with other contracts.
Reentrancy Guard: A reentrancy guard is a mechanism to ensure that a function cannot be re-entered while it is still executing. This is crucial for preventing reentrancy attacks, where an external call to another contract could re-enter the current function.
Therefore, the crux of the matter isn't the ERC777 token standard itself. Instead, the issues often stem from how developers implement their contracts that interact with these tokens.
When not carefully coded, especially without consideration for reentrancy and the secure patterns of contract interactions, vulnerabilities can be introduced. This means that it is not the problem of implementing ERC777 tokens but rather writing smart contracts with bad design.