Like other threats in the Web3 space, one particularly insidious type of scam that has gained notoriety is known as the "pig butchering" scam. The idea behind the term refers to being kind to the pig by offering extra food for selfish and malicious reasons. According to a 2022 FBI report, Americans reported over $700 million to romance scams in both crypto and fiat.
This attack preys on the user's lack of knowledge and experience while leveraging sophisticated social engineering techniques to build trust before ultimately exploiting it. Although it originated from traditional finance, it now has a place in the crypto communities.
It is a social engineering attack that involves scammers tricking users into making a series of unwise investments that earn money for the attacker after they have created some kind of rapport to gain their Victim's trust, friendship, or even romantic interest.
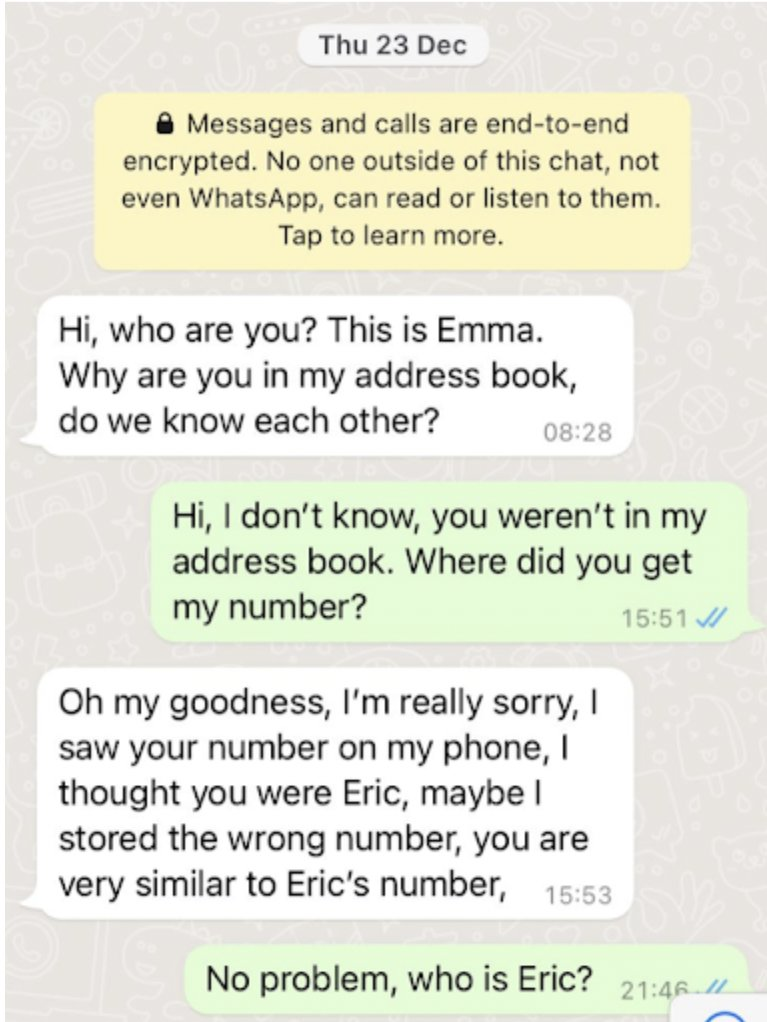
In some cases, The scammer begins by pretense that suggests that they have reached out to a wrong number or that they have the victim’s number saved by a name they are familiar with. By this strategy, they engage their target and build a very friendly ambiance around their falsified identity in order to build trust.
They also conduct background checks on their targets that help them identify their points of interest so as to present themselves as having similar experiences. This engineering targets the tendency for humans to resonate with and trust people that they have similarities with.
The Human nature In the play
Humans are inherently social and emotional beings, traits that scammers skillfully exploit. Even individuals who are generally cautious and savvy can find themselves vulnerable when they step into the unfamiliar, often confusing world of cryptocurrency and self-custody. The promise of romance, friendship, respect, or a sense of belonging can cloud judgment and lead to irrational decisions. Scammers understand that these social factors are powerful motivators.
This attack preys on the user's lack of knowledge and experience while leveraging sophisticated social engineering techniques to build trust before ultimately exploiting it. Although it originated from traditional finance, it now has a place in the crypto communities.
It is a social engineering attack that involves scammers tricking users into making a series of unwise investments that earn money for the attacker after they have created some kind of rapport to gain their Victim's trust, friendship, or even romantic interest.
In some cases, The scammer begins by pretense that suggests that they have reached out to a wrong number or that they have the victim’s number saved by a name they are familiar with. By this strategy, they engage their target and build a very friendly ambiance around their falsified identity in order to build trust.
They also conduct background checks on their targets that help them identify their points of interest so as to present themselves as having similar experiences. This engineering targets the tendency for humans to resonate with and trust people that they have similarities with.
The Human nature In the play
Humans are inherently social and emotional beings, traits that scammers skillfully exploit. Even individuals who are generally cautious and savvy can find themselves vulnerable when they step into the unfamiliar, often confusing world of cryptocurrency and self-custody. The promise of romance, friendship, respect, or a sense of belonging can cloud judgment and lead to irrational decisions. Scammers understand that these social factors are powerful motivators.
Once trust is established, the scammer gradually introduces the idea of investing in cryptocurrency, often presenting it as a lucrative opportunity. They might guide the victim through setting up accounts on legitimate-looking platforms or even persuading them to transfer funds to the scammer's wallet for "investment purposes." By the time the victim realizes they have been duped, it is often too late; their funds are gone, and the scammer has disappeared.
How to Protect Yourself Against Pig Butchering Scams
To safeguard yourself against pig butchering scams and other forms of social engineering attacks, be on the lookout for these common red flags and take the following preventive measures:
1. Avoid Rapid Relationship Development
Be cautious if someone you've just met online quickly expresses strong feelings or a desire to help you financially. Scammers often try to build trust and emotional connections rapidly to manipulate their victims more easily.
2. Verify Identities
Always verify the identity of individuals you interact with online. Use trusted platforms and be skeptical of unsolicited contacts. Avoid sharing personal information with strangers.
3. Resist Pressure to Act Quickly
Legitimate investments don't require immediate action. Be wary of anyone pushing you to invest right away, as this is a common tactic used by scammers to prevent you from thoroughly researching the opportunity.
4. Watch When There’s Reluctance to Video Chat
If your new online friend always has an excuse not to video chat, they may be hiding their true identity. Video chatting can help verify that the person is who they claim to be. Reluctance or refusal to video chat is a significant red flag.
5. Be Cautious with Requests for Personal or Financial Information
Legitimate investment platforms won't ask for sensitive data through informal channels. Be very cautious if someone requests your personal or financial information, especially if the request comes through unofficial means like email or messaging apps.
6. Research Investment Opportunities
Conduct thorough research on any investment opportunities before committing funds. Look for reviews, verify the legitimacy of the platform, and seek advice from trusted sources. Be wary of investments that promise unusually high returns with little to no risk.
