Ether Transfers in Solidity: transfer(), send(), and call()
Introduction
Transferring Ether in Solidity can be accomplished using three main methods: transfer(), send(), and call(). Each method behaves differently in terms of gas forwarding, error handling, and security. In this post, we’ll explore these methods, review code examples, and discuss best practices for ensuring secure Ether transfers in your smart contracts.
For professional assistance with smart contract security and audits, consider exploring Bailsec's audit services.
1. transfer()
How It Works
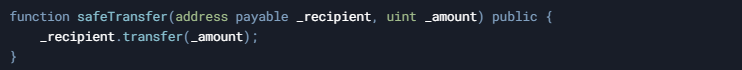
The transfer() method is considered the simplest and most secure way to send Ether. It forwards exactly 2300 gas to the recipient, which is generally enough only for logging or minimal fallback operations, thereby minimizing reentrancy risks. If the transfer fails (for instance, if the recipient's fallback function consumes more than 2300 gas), the entire transaction is automatically reverted.
Key Points:
- Gas Forwarding: Only 2300 gas is forwarded.
- Error Handling: Automatically reverts on failure.
- Security: Helps prevent reentrancy attacks.
Note: Some auditors worry about using transfer() if a smart contract wallet is involved. This method only reverts if there is gas-consuming logic in the fallback or receive function. For more details on smart contract safety, see our security reviews.
2. send()
How It Works
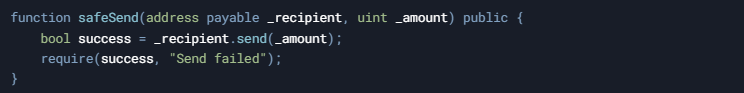
The send() method behaves similarly to transfer() in that it also forwards 2300 gas. However, it does not automatically revert if the transfer fails—instead, it returns a boolean value. This requires you to manually check the return value and handle any failure cases.
Key Points:
- Gas Forwarding: 2300 gas is forwarded.
- Error Handling: Returns a boolean, so errors must be handled manually.
- Security: Similar reentrancy protection as transfer().
For more advanced error handling techniques, review our workflow documentation.
3. call()
How It Works
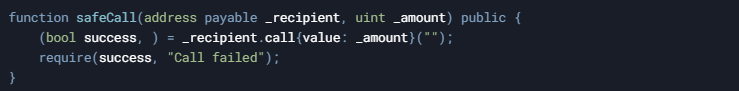
The call() method is the most flexible way to send Ether, as it forwards all available gas by default and allows for arbitrary function calls. However, this flexibility comes at a cost—it is more vulnerable to reentrancy attacks if not properly guarded. As with send(), you must check the return value to ensure that the transfer succeeded.
Key Points:
- Gas Forwarding: Forwards all available gas unless specified otherwise.
- Error Handling: Returns a boolean; manual checking is required.
- Security: Higher reentrancy risk; always combine with reentrancy guards (e.g., using a nonReentrant modifier).
Tip: When using call(), consider setting a custom gas limit and using patterns like checks-effects-interactions to mitigate risks.
Security Considerations
Reentrancy Attacks
- transfer() and send() minimize reentrancy risks by forwarding only 2300 gas.
- call() forwards all gas, increasing the reentrancy risk. Always protect calls with proper checks or a nonReentrant modifier.
Error Handling
- transfer() automatically reverts on failure, simplifying error management.
- send() and call() require explicit checking of their return values. Failing to do so can lead to silent failures and potentially lost funds.
Gas Management
- transfer() and send() limit gas usage to 2300, which may be insufficient for certain fallback functions.
- call() offers more flexibility in gas forwarding but must be handled carefully.
For further insights into how to optimize your contracts while maintaining security, check out our detailed security reviews.
Best Practices
- Choose the Right Method:
- Use transfer() when simplicity and built-in error handling are sufficient. Use send() when you need custom error handling, and call() when interacting with contracts that require more than 2300 gas.
- Always Check Return Values:
- For both send() and call(), always verify the returned boolean value to confirm that the transfer was successful.
- Implement Security Patterns:
- Utilize the checks-effects-interactions pattern or nonReentrant modifiers to safeguard against reentrancy attacks.
- Custom Gas Management:
- When using call(), specify a custom gas limit if needed and test extensively under different conditions.
For more detailed guidance on secure smart contract development, visit Bailsec's services page.
Conclusion
Selecting between transfer(), send(), and call() depends on your contract's requirements for gas, error handling, and security. While transfer() is simple and secure for most basic transfers, send() and call() offer greater flexibility when used with proper checks and safeguards.
Understanding these methods and their implications is essential for writing robust and secure smart contracts on Ethereum. For professional security audits and further consultation on optimizing your smart contract design, consider reaching out to Bailsec. Also, check out our blog for more in-depth articles on Solidity security and best practices.
Disclaimer: This post is for informational purposes only and does not constitute legal or financial advice. Always perform thorough testing and consider professional audits to ensure your smart contracts are secure.
